
Keeping video data safe in the cloud doesn't have to be complicated. Modern cloud video management systems blend smart security features like encryption and multi-step login checks with practical storage solutions that work both online and at your cameras. While these systems make it easy to watch and manage videos from anywhere, they need proper protection - just like a house needs good locks and an alarm system.
By setting up the right mix of security tools and following data privacy rules, you can build a reliable cloud video system that keeps recordings safe without sacrificing easy access.
Key Takeaways
- Implement end-to-end encryption for video streams and stored footage while ensuring compliance with data protection regulations like GDPR and HIPAA.
- Deploy multi-factor authentication and role-based access control to prevent unauthorized access to cloud-stored video content.
- Utilize edge devices for local video compression and encryption before transmission to reduce security vulnerabilities during data transfer.
- Set up automated monitoring systems with real-time alerts for detecting and responding to potential security breaches.
- Integrate blockchain technology for tamper-proof video storage and maintain comprehensive access logs for security auditing.
💡 Ready to implement these security measures in your video management system?
Our team has 19+ years of experience in developing secure video solutions. See our past projects or schedule a free consultation to discuss your specific requirements.
Understanding Cloud VMS Fundamentals

Cloud Video Management Systems (VMS) combine distributed storage, secure streaming protocols, and intelligent analytics to process and manage your video data through web-based interfaces.
Modern cloud VMS architectures typically include edge devices for local recording, cloud servers for processing and storage orchestration, and APIs that enable seamless integration with your existing security infrastructure.
When compared to traditional on-premise solutions, cloud VMS offers you greater scalability, automatic updates, and reduced maintenance overhead while supporting remote access from any authorized device.
Recent studies have shown that cloud-based solutions can achieve up to 90% resource utilization efficiency, significantly outperforming traditional on-premise systems that typically operate at around 60% efficiency (Liu et al., 2021).
How Cloud Video Management Systems Work
Modern video management systems operate by seamlessly integrating three core components: data ingestion from cameras, cloud-based processing infrastructure, and user access interfaces.
Your cloud video management system continuously receives and processes security footage through edge devices, which compress and encrypt data before transmission. The cloud-based system then analyzes this input using AI algorithms to generate actionable intelligence.
Your video management software makes this data accessible through web portals and mobile apps, enabling real-time monitoring and historical review. The thoughtful design of cloud infrastructure significantly enhances how users interact with these services, leading to more efficient operations and improved service delivery (Bernal et al., 2019).
Advanced features include automated alerts, motion detection, and integration with other security platforms.
Key Components and Architecture
Building a strong video management system requires understanding its foundational elements and how they work together. Your cloud video surveillance platform needs these essential components to deliver advanced system features effectively.
Key architectural elements include:
- Distributed cloud infrastructure for scalable processing
- Secure storage systems with redundancy
- Video management system software for stream handling
- API layers for third-party integrations
The architecture should support real-time video processing while maintaining data integrity.
When designing your system, prioritize modularity to allow for future expansion. Consider implementing microservices to handle different aspects of video processing, storage, and retrieval independently.
Benefits of Cloud vs. On-Premise Solutions
When deciding between deployment options for your video management system, understanding the distinct advantages of cloud-based solutions compared to traditional on-premise installations becomes essential.
Cloud-based video surveillance offers notable benefits through remote access capabilities, letting you monitor and manage your system from anywhere. You'll reduce infrastructure costs while gaining automatic updates and scalable video surveillance storage.
A cloud solution enables advanced analytics integration without additional hardware investments. You can implement AI-powered features, facial recognition, and motion detection more easily than with on-premise systems.
The platform handles maintenance and security updates automatically, freeing your team to focus on core business operations.
Our experience with V.A.L.T demonstrates these benefits in practice. Medical education institutions using our system particularly value the scalability, as they can easily add cameras and facilities without additional hardware investments.
🔐 Wondering how to make the switch to a secure cloud-based video management system? Our experts can help you navigate the transition seamlessly. Learn about our AI integration services or contact us for a personalized assessment.
Modern Security Framework for Cloud VMS
Your cloud VMS solution must incorporate strong data protection measures, including end-to-end encryption and secure access controls, to safeguard sensitive video content from unauthorized access.
You'll need to guarantee your system complies with industry-specific regulations like GDPR, HIPAA, or CCPA, depending on your deployment region and use case. Implementing privacy-enhancing features such as automated data retention policies and user consent management will help you maintain both regulatory compliance and user trust.
For instance, in our V.A.L.T project, we implemented SSL and RTMPS encryption to protect client-server data and video streams, particularly crucial for sensitive use cases like police interrogations and medical consultations. The system's severe access control ensures that medical students can only access their own patient consultation videos, preventing unauthorized access to sensitive patient information.
Essential Data Protection Measures
To protect your cloud-based video management system, you'll need to implement strong end-to-end encryption for all video streams and stored footage using industry standards like AES-256.
Studies show that AES-256 encryption can be effectively implemented even in resource-constrained environments while maintaining robust security levels and achieving significant power efficiency, making it an ideal choice for cloud-based video systems (Duran et al., 2021).
Your access control strategy should incorporate multi-factor authentication and role-based permissions to guarantee only authorized personnel can view or manage specific video resources.
Consider integrating Single Sign-On (SSO) capabilities and maintaining detailed access logs to track user interactions while supporting compliance requirements for your video management platform.
End-to-End Encryption Standards
Implementing end-to-end encryption standards in cloud-based video management systems forms the foundation of secure data transmission and storage. Your cloud platform should integrate strong encryption protocols for video surveillance technology.
Key encryption requirements for your cloud-based VMS:
- Use TLS 1.3 or higher for secure connections
- Implement AES-256 encryption for stored content
- Enable perfect forward secrecy (PFS)
- Maintain client-side encryption keys
Access Control and Authentication
A strong access control and authentication system serves as the cornerstone of any secure cloud-based video management solution. You'll need to implement multi-factor authentication for your cloud service, ensuring users verify their identity through multiple checkpoints. When managing video surveillance data, assign role-based permissions to control who can access, modify, or extract actionable intelligence from your footage.
For instance, in V.A.L.T's implementation for medical education institutions, we developed granular permission controls ensuring supervisors can only access videos of their assigned students, while students are restricted from accessing other students' patient consultation recordings.
Compliance and Privacy Requirements
You'll need to prioritize GDPR and CCPA compliance in your cloud-based video management system by implementing user consent mechanisms and clear data handling policies. Your VMS should include features that allow users to exercise their privacy rights, such as data access requests, the right to be forgotten, and data portability options.
To meet data retention requirements, you'll want to establish automated retention periods and deletion workflows that align with both regulatory standards and your business needs.
GDPR and CCPA Implementation
When developing cloud video management systems, data privacy regulations like GDPR and CCPA create essential frameworks that protect user rights while shaping your development approach.
To meet regulatory requirements for video surveillance footage and cloud storage, implement these controls:
- Build automated data deletion workflows
- Create transparent access control systems
- Implement user consent management features
- Design data portability tools for enhanced customer experience
Data Retention Strategies
Building upon privacy regulations, effective data retention strategies form the foundation of compliant cloud video management systems. You'll need to configure your security camera systems with automated policies that determine how long to store footage.
Implement video analytics to flag and extend storage for slip-and-fall incidents, while establishing standard retention periods for routine recordings in your cloud video security system.
Advanced Development Strategies

You'll find considerable advantages in implementing serverless computing for your cloud-based video management system, as it eliminates the need to manage infrastructure while automatically scaling to meet demand.
Incorporating containerization lets you package your application components consistently across different environments, making deployments more reliable and easier to maintain.
Through container orchestration tools like Kubernetes, you can efficiently manage these containerized applications, automate their deployment, and guarantee high availability for your video management service.
⚡ Looking to modernize your video management infrastructure?
Let's discuss how our serverless and containerization expertise can transform your system. Book a call to explore the possibilities.
Serverless Computing Integration
Integrating serverless computing through Lambda functions can transform your video management system by automating essential processing tasks without maintaining dedicated servers. An event-driven architecture enables your system to respond automatically to user actions, such as uploading new videos or requesting format conversions.
Lambda Functions for Video Processing
Lambda functions revolutionize video processing workflows by enabling automated, event-driven operations without maintaining dedicated servers. This shift reflects a broader industry trend, as serverless computing has driven significant workload migrations, particularly in video processing and machine learning applications (Kaffes et al., 2021). You'll gain actionable business intelligence through intelligent alerts as your video footage processes in real-time during cloud transmission.
Key implementation benefits include:
- Automatic scaling based on processing demands
- Pay-per-use cost efficiency
- Real-time video analytics integration
- Simplified deployment and maintenance
Event-Driven Architecture
Building upon serverless video processing capabilities, event-driven architecture forms the foundation of modern cloud-based video management systems. Cloud providers now offer integrated solutions where security cameras can trigger automated responses. When specific events occur, your system can generate real-time alerts, making it easier to scale and adjust to the video surveillance industry's evolving needs.
Containerization and Orchestration
Implementing Docker containers for your video management system will help you standardize deployment across different cloud environments while isolating individual components for better security and scalability.
Kubernetes orchestration provides automated deployment, scaling, and management of your containerized video applications, ensuring consistent performance even during peak usage periods.
Docker and Kubernetes Implementation
To enhance the scalability and portability of your video management system, Docker containers and Kubernetes orchestration provide essential infrastructure modernization tools. These robust integration tools enable efficient cloud deployment and streamlined software updates.
Specifically, they allow you to:
- Package applications with all dependencies in isolated containers
- Automate container deployment and scaling across clusters
- Monitor and manage container health in real-time
- Implement rolling updates with zero downtime
Multi-Cloud Deployment
While Docker and Kubernetes provide strong containerization solutions, a multi-cloud deployment strategy expands your system's resilience and flexibility even further.
You can implement a central platform that manages your true cloud video surveillance across multiple providers through a cloud gateway. This approach strengthens your security measures by distributing resources and reducing single points of failure.
Case Study: V.A.L.T - Enterprise-Grade Video Management System
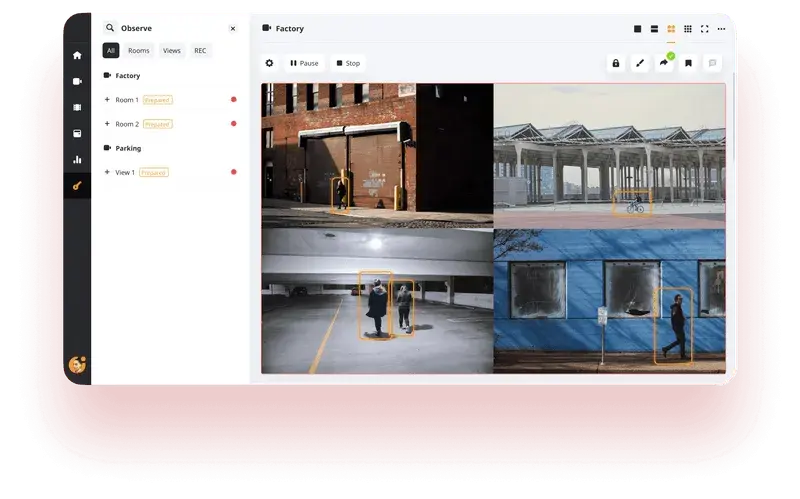
When developing V.A.L.T, our team focused on creating a scalable, secure, and user-friendly video management solution. The system currently serves over 450 client organizations, including police departments, medical institutions, and child advocacy organizations, each with unique security and functionality requirements.
Key Development Insights:
- We prioritized intuitive interface design, resulting in a system that new users can master in just 10 minutes
- Implemented modular architecture allowing unlimited users and cameras without extensive IT resources
- Developed specialized features like automated scheduling and hardware controls for specific use cases
- Integrated advanced security measures while maintaining high-quality HD video streaming capabilities
This system demonstrates how proper architecture and security implementation can support diverse enterprise needs while maintaining simplicity for end-users.
Next-Generation Features
Integrating AI and machine learning into your cloud video management system can reveal potent capabilities like automated object detection, behavior analysis, and predictive maintenance. Connecting your system with IoT platforms creates seamless interactions between video feeds and smart devices, facilitating automated responses to detected events.
These technological integrations can transform your basic video management solution into an intelligent security ecosystem that adjusts and responds to real-world situations.
AI and Machine Learning Integration
Integrating AI and machine learning into your cloud-based video management system can enhance security through automated threat detection and real-time monitoring of suspicious activities. You'll need to carefully consider the ethical consequences of AI implementation, including data privacy, bias prevention, and transparency in algorithmic decision-making.
Your development roadmap should include clear guidelines for AI model training, regular auditing of detection accuracy, and user consent protocols that align with current privacy regulations and industry best practices.
Automated Threat Detection
As cloud-based video management systems evolve, automated threat detection driven by AI and machine learning has become an essential security component. Your robust cloud video surveillance system can utilize artificial intelligence to identify potential threats in real-time, offering:
- Instant intrusion detection alerts
- Behavioral pattern analysis
- Suspicious activity monitoring
- Network connection anomaly detection
These features enable proactive security measures rather than reactive responses.
Ethical AI Considerations
While AI-driven video management systems offer powerful capabilities, they must be developed with strong ethical guidelines to protect user privacy and prevent misuse. Your cloud systems should anonymize personal information in video recordings, and you'll need clear protocols for security personnel accessing the data. Consider implementing AI oversight tools that monitor customer service interactions and flag potential privacy violations.
IoT Platform Integration
You'll want to connect your video management system to your building's IoT infrastructure, enabling seamless integration with smart sensors, access control systems, and environmental monitors.
By utilizing IoT platform integration, you can implement predictive maintenance algorithms that alert you to potential camera failures or network issues before they impact your security coverage.
Your development team can create custom APIs to establish real-time data exchange between your video management software and IoT devices, enhancing both security monitoring and building automation capabilities.
We've implemented this in V.A.L.T through hardware controls that allow users to control recording directly from the room, including 'In Use' signs that automatically illuminate when recording begins - a crucial feature for police interrogation rooms.
Smart Building Connectivity
Modern smart building initiatives benefit considerably from integrating cloud-based video management systems with IoT platforms. Cloud adapters enable unlimited users to access meaningful perspectives through advanced loss prevention tools. Your access control integrations can support:
- Real-time occupancy monitoring
- Automated security responses
- Environmental control optimization
- Cross-platform data synchronization
Predictive Maintenance Capabilities
Integrating predictive maintenance capabilities with your cloud-based video management system creates strong opportunities for proactive equipment monitoring and cost reduction.
Implementation Best Practices

To strengthen your cloud-based video management system, you'll need a solid CI/CD pipeline that automates testing, deployment, and monitoring processes. Your development workflow should incorporate thorough security testing at each stage, including automated vulnerability scans, penetration testing, and code analysis tools.
You'll also want to establish clear incident response procedures that outline steps for identifying, containing, and resolving security issues while maintaining system availability.
CI/CD Pipeline Setup
While building secure video management systems in the cloud, a well-structured CI/CD pipeline serves as the foundation for consistent, reliable deployments. You'll need to integrate security checks at every stage of your development process, from code commits to deployment on remote servers.
This comprehensive approach involves several key steps:
- Configure automated security scans that detect vulnerabilities in your video processing code
- Implement access control mechanisms that validate user permissions before deployment
- Set up automated testing for your robust search tools and indexing features
- Establish monitoring systems that track pipeline performance and security metrics
Ensure your pipeline includes proper error handling and rollback procedures for failed deployments, maintaining system integrity throughout the development lifecycle.
Security Testing and Monitoring
Effective security testing and monitoring form the foundation of any reliable cloud-based video management system.
You'll need to implement automated scanning tools to detect potential vulnerabilities in your security videos storage and access control solution. Regular penetration testing helps identify weaknesses before attackers do.
Configure alerts for unusual patterns, including recorder malfunction events and unauthorized access attempts. Set up monitoring dashboards to track cloud resource usage and guarantee compliance with retention periods. Implement continuous security assessments that evaluate encryption strength, access logs, and authentication mechanisms.
This proactive approach helps maintain system integrity while protecting sensitive video assets.
Incident Response Planning
Building upon strong security testing, a well-structured incident response plan serves as your defense blueprint when security events occur. When managing cloud-based video systems, you'll need specific protocols for different security scenarios. Key components to include in your incident response planning:
- Automated alerts for unauthorized access control attempts
- Dedicated response teams with clear roles for handling video management breaches
- Step-by-step procedures for containing and isolating affected cloud resources
- Communication protocols for notifying stakeholders and affected users
Document and regularly update these procedures, ensuring your team can respond swiftly to security events. Consider implementing tabletop exercises to test your response effectiveness.
Future-Proofing Your Cloud VMS
To future-proof your cloud video management system, you'll want to implement emerging compression technologies like AV1 and VVC that can greatly reduce storage costs while maintaining quality.
Edge computing applications will let you process video data closer to the source, reducing latency and bandwidth requirements for your cloud infrastructure.
You can also enhance video integrity and chain-of-custody verification by incorporating blockchain technology into your system's architecture, ensuring tampering resistance and maintaining an unchangeable record of video authenticity.
Emerging Video Compression Technologies
Modern video compression standards evolve rapidly, creating both opportunities and challenges for cloud-based video management systems (VMS).
You'll need to evaluate emerging compression technologies to optimize your access control platform and centralized recorders while managing growing amounts of video data. Consider these key compression technologies for your cloud VMS:
- H.265/HEVC offering up to 50% better compression than H.264
- AV1 providing royalty-free, efficient compression for streaming
- VVC/H.266 delivering improved quality at lower bitrates
- AI-powered codecs using machine learning for flexible compression
Implementing these technologies can greatly reduce storage costs while maintaining video quality across your cloud infrastructure.
Edge Computing Applications
While advanced compression technologies help manage cloud storage demands, edge computing brings video processing closer to the source. Your IP cameras can process footage locally, reducing bandwidth requirements and latency in your cloud video management system. Edge computing solutions can reduce video data transmission to cloud nodes by up to 99.5%, significantly lowering bandwidth requirements for video management systems (Sun et al., 2020).
By implementing edge computing solutions, you'll enable real-time analytics and access control decisions at the device level. Consider deploying smart cameras with built-in processing capabilities. They'll analyze video streams instantly, identifying relevant events before sending only essential data to your cloud infrastructure.
This distributed approach enhances system reliability and reduces operational costs while maintaining strong security features. You'll achieve faster response times and more efficient resource utilization.
Blockchain for Video Integrity
Blockchain technology provides a strong foundation for ensuring video integrity in cloud-based management systems. The technology's scalable nature makes it particularly effective for handling extensive video data across surveillance and streaming applications without compromising integrity (Donawa et al., 2019).
You'll benefit from implementing blockchain to maintain a secure chain of custody for your video recordings. When integrated with your cloud VMS, it creates tamper-proof records of all video access and modifications.
Key features of blockchain-based video integrity:
- Immutable audit trails for every recording mode change
- Cryptographic verification of original footage
- Automated access control logging
- Time-stamped proof of video authenticity
Measuring Success and ROI
To measure the success of your cloud video management system, you'll need to track key performance indicators like video stream latency, storage efficiency, and user adoption rates. You can evaluate security effectiveness through metrics such as incident response times, successful threat preventions, and compliance audit scores.
Performance Metrics
Measuring the success of cloud-based video management solutions requires an extensive set of performance metrics that align with both technical capabilities and business objectives.
Your video management system's performance should be tracked through these essential indicators:
- Response time for video access control and playback functions
- System uptime and reliability percentages across cloud servers
- Storage efficiency and compression ratios for video files
- Audio analytics accuracy rates and false positive metrics
In developing V.A.L.T, we focused on key performance indicators like HD video streaming quality, supporting up to 9 IP cameras simultaneously on one screen while maintaining perfect audio-video synchronization
Security Benchmarks
Security benchmarks serve as critical indicators for evaluating your cloud video management system's protective measures and return on investment.
You'll need to track access control events and monitor user authentication success rates to guarantee proper system usage. Implement hybrid cloud solutions to maintain both instant access and physical security of your data centers.
To measure security effectiveness, establish baseline metrics for unauthorized access attempts, encryption status, and data breach prevention.
These benchmarks provide peace of mind by quantifying your system's resilience against threats. Consider tracking recovery time objectives, backup success rates, and compliance audit scores to demonstrate your security infrastructure's value.
Cost Optimization Strategies
Building on your established security metrics, cost optimization becomes the next key performance indicator for cloud video management systems.
You'll find substantial cost savings by implementing efficient resource allocation and smart scaling strategies. A consistent internet connection helps maintain ideal performance while keeping additional costs in check.
Key areas to focus on for cost-effective video management:
- Implement auto-scaling for unlimited sites without overprovisioning
- Choose access control affordable solutions with pay-as-you-go models
- Monitor bandwidth usage and compress video streams when possible
- Employ storage tiering to balance performance and costs
Regular cost analysis guarantees your cloud video management system remains financially efficient while maintaining security standards.
Why Trust Our Cloud Video Management Expertise?
With over 19 years of specialized experience in multimedia development and video streaming solutions, we've been at the forefront of cloud-based video management innovation since 2005. Our team has successfully implemented secure video management systems for over 450 client organizations, including police departments, medical institutions, and child advocacy organizations - each with unique security requirements and compliance needs.
Our expertise in video streaming technologies, coupled with our deep understanding of AI integration and security protocols, has earned us a 100% project success rating on Upwork. We've developed and refined our approach through countless implementations, from small-scale deployments to enterprise-level solutions handling multiple simultaneous HD video streams with perfect audio-video synchronization. This hands-on experience informs every recommendation and best practice shared in this guide.
Frequently Asked Questions
How Do You Handle API Rate Limiting for Large-Scale Video Streaming Deployments?
You'll need to implement token bucket algorithms, use Redis for rate tracking, and set tiered limits based on user plans. Configure retry mechanisms and provide clear rate headers in API responses.
What Encryption Protocols Are Recommended for Video Data at Rest?
You'll want to implement AES-256 encryption for stored video files, while using XTS mode for better security. Consider utilizing AWS KMS or Azure Key Vault to manage your encryption keys and access controls.
Can Legacy Camera Systems Integrate With Modern Cloud VMS Architectures?
You can integrate legacy cameras through network video encoders or API bridges. Using ONVIF-compliant converters, you'll transform analog signals to digital streams that'll work with modern cloud VMS platforms.
How Are Video Analytics Modules Deployed Across Multiple Cloud Regions?
You'll need to deploy analytics containers in each region, using orchestration tools like Kubernetes. Configure load balancers to route video streams to the nearest analytics instance for efficient processing and reduced latency.
What's the Recommended Approach for Handling Offline-To-Online Video Data Synchronization?
You'll want to implement a queue-based system with delta synchronization, where your app caches offline changes locally and syncs incrementally when connectivity returns. Use background workers to handle conflict resolution efficiently.
To Sum Up
Securing your cloud-based video management system isn't a one-time effort but an ongoing process. You'll need to regularly update security protocols, monitor emerging threats, and modify your infrastructure to meet evolving compliance requirements. By implementing strong encryption, access controls, and continuous monitoring, you're building a resilient foundation for your VMS. Remember to measure security metrics and user experience to guarantee your system remains both secure and functional.
🚀 Ready to secure your video management system with industry-leading expertise?
Our team is here to help you implement these best practices and more. View our portfolio or schedule a consultation to get started on your project today.
References:
Bernal, A., Cambronero, M., & Valero, V. et al. (2019). A framework for modeling cloud infrastructures and user interactions. IEEE Access, 7, pp. 43269-43285. https://doi.org/10.1109/access.2019.2907180
Donawa, A., Orukari, I., & Baker, C. (2019). Scaling blockchains to support electronic health records for hospital systems. In IEEE Conference on Ubiquitous Computing, Electronics & Mobile Communication (UEMCON), 0550-0556. https://doi.org/10.1109/uemcon47517.2019.8993101
Duran, C., Gomez, H., & Roa, E. (2021). AES SBox acceleration schemes for low-cost SoCs. In IEEE International Symposium on Circuits and Systems (ISCAS). https://doi.org/10.1109/iscas51556.2021.9401539
Kaffes, K., Yadwadkar, N., & Kozyrakis, C. (2021). Practical scheduling for real-world serverless computing. arXiv preprint. https://doi.org/10.48550/arxiv.2111.07226
Liu, D., Peng, J., & Zhang, X. et al. (2021). Application features‐based virtual machine deployment strategy in cloud environment. Concurrency and Computation: Practice and Experience, 34(5). https://doi.org/10.1002/cpe.6691
Sun, H., Yu, Y., & Sha, K. et al. (2020). MVideo: Edge computing based mobile video processing systems. IEEE Access, 8, pp. 11615-11623. https://doi.org/10.1109/access.2019.963159













.avif)

Comments